Urgent Security Fixes Issued for Windows, Adobe Flash Player & AIR

Windows
The usual round of updates are in. As today is Patch Tuesday, Windows and Adobe Flash and Air were issued security updates. Microsoft had seven update bundles containing 20 total vulnerabilities in Windows and other Windows software. Adobe released updates for Flash and Air.
Microsoft had four critical patches, and three other updates. A total of seven today.
The critical patches address bugs in Windows, Internet Explorer, Microsoft Silverlight, Microsoft Office and Microsoft SharePoint. Updates are available for Windows XP, Vista, Windows 7, Windows 8, Windows Server 2003, 2008 and 2012.
Either you will receive Automatic Updates, if you’ve set Windows up to do so. Otherwise, go to Start, search Windows Update. Or for Windows 8, search for Windows Update on the Start screen.
Adobe Flash Player/AIR
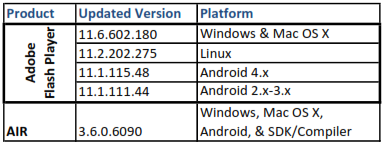
Adobe has sent updates for Flash Player, now at 11.6.602.180. This is the version for Windows and Mac OS X based systems. Four security flaws were identified, which prompted this fix. No current attacks/exploits have been identified.
Keep in mind that Google Chrome and Internet Explorer 10 (Windows 8) automatically update Flash Player on their own. The update may not be issued for Chrome just yet, but should be soon, we hope.
If you have Adobe AIR installed, which is required for quite a few programs that are built on its architecture (such as Tweetdeck, Pandora Internet Radio, games, etc.). AIR should automatically prompt to update.
Here is the update table for Adobe Flash Player and AIR:
Adobe’s Patch Tuesday for Acrobat/Reader – ColdFusion Problems
Adobe will release a round of updates on Patch Tuesday (as usual). This month, Patch Tuesday (which involves Microsoft and Adobe, sometimes Oracle) will be on January 8. It’s first updates involve vulnerabilities in Reader and Acrobat products, while the other issues involve ColdFusion vulnerabilities.
“Adobe is aware of reports of security issues in ColdFusion 10, 9.0.2, 9.0.1 and 9.0 for Windows, Macintosh and UNIX that are being exploited in the wild. We are currently evaluating the reports and plan to issue a security advisory as soon as we have determined mitigation guidance for ColdFusion customers and a timeline for a fix,” said Adobe’s Wendy Poland in an advisory posted January 3.
From the good news side of things, none of these vulnerabilities are being actively exploited in the wild. But, let’s not get too hasty to underestimate threats. Make sure to get patched on Tuesday!
Vulnerabilities in Adobe Reader and Acrobat versions 11.0.0 and earlier are going to be patched next week.
Last month, there were issues in Flash Player and ColdFusion. Looks like these are favorites of hackers as of late.
Protect yourself from vulnerabilities with Kaspersky ONE Security, one good price ($79.95) per year for awesome protection.
Will 2013 Be a Challenging Year for Computer Security?
Much of the attention in 2013 in computer security will be mainly focused on industrial control systems (ICS), Android, and the all new Windows 8 OS. With the dealings of malware like Stuxnet and other government threats, to the normal hackers and attackers on consumer devices – it will be a challenge in both business and consumer markets.
Supervisory software runs on dedicated workstations and programmable hardware devices, and this is called a control system. They’re used to monitor and control many different operations, such as power grids, trains, airplanes, water distribution systems, military installations, and many more. Many times, control systems are used in critical infrastructures, especially systems for big populations that depend on electricity, clean water, transportation, etc.
Many worries that we’d be watching in 2013 that other security authorities are watching as well include the rise of more government malware. Especially, when it comes to control systems, which are believed to be widely targeted and surveyed.
For other problems to be faced include intense rises of mobile malware, particularly in the Android marketplace. The problem is that Android malware is becoming more widespread. It looks like hackers are retrying some old methods of Windows operating system exploitation on Android devices. This can prove to become a big problem to watch out for.
The big issue with Android attacks also seems to point at privilege escalation attacks, which like to work through malicious apps installed by the user to gain root access and take control of the device. With hundreds of millions of Android devices already infected since its birth, the size of botnets have gotten to be big, and there may still be a lot of devices infected.
Also, keep in mind that when you use a smartphone, you’re leaking a lot of information. This is mainly through App usage, which most of them collect a bit of data from your phone. It isn’t exactly personally-identifiable information, however, it’s enough to make some people nervous.
Android is very open, and you can download apps from almost anywhere for Android. This is much like Windows OS has been. But, that’s a whole different long story.
Windows 8 will be a challenge for security, because researchers, hackers, security experts, etc. want to get in on testing just how secure it is.
Google Releases Chrome 23.0.1271.97
Google released a new update for the stable version of Chrome, now at version 23.0.1271.97. All of the supported platforms have an update: Windows, Mac, Linux, and Chrome Frame.
One the issues fixes is involved with a website settings popup having texts trimmed under certain conditions. Another problem fixed involves a Linux bug and consists of <input> selection rendering white text on a white background making the string invisible. Also, repaired is the issue with plugins such as Google Voice and Unity Player that would stop working. This revision also includes the latest version of Adobe Flash.
Check for the latest Chrome download on www.google.com/chrome or in the Chrome browser, hit the settings button on the top right, select About Google Chrome. Usually, Google Chrome updates are automatically applied using Google Updater.
Adobe Issues Critical Security Updates for Flash and AIR
Election Day brings Adobe’s critical updates for Flash and AIR, so update today to fix seven (7) vulnerabilities.
Updates are currently available as follows:
FLASH
- Windows & Mac – 11.5.502.110
- Linux – 11.2.202.251
- Android 4.* – 11.1.115.27
- Android 3.* & 2.* – 11.1.111.24
- Google Chrome automatically updates the Flash version built in.
AIR
- Windows, Mac, SDK for iOS and Android – 3.5.0.600
Be sure to download the Flash updates for both Internet Explorer, and then for Firefox/Safari/Opera/Other browsers.
Also, note Windows Update will help install the updates in Windows 8/IE 10, reference here
Critical fix issued for Shockwave Player – Oct. 23, 2012
Adobe has released a critical update for Shockwave Player after several serious vulnerabilities were found.
- Users of 11.6.7.637 and earlier versions should now update to version 11.6.8.638 – Update Now

- Updates are available for Windows and Mac systems.
- There is no active propagation of exploits.
- Check to see if you have Shockwave Player.
- Shockwave Player is not the same as Adobe Flash Player, which update October 8.
- Check release notes.
- Uncheck the Norton Security Scan, if it shows.
To protect against vulnerabilities, it is best to have a good internet security software, not FREE antivirus! Check here:
Steam Gamers Listen Up: Platform Vulnerable to Remote Exploits, 50M at risk
50 million users plus of the Steam gaming and distribution platform are at risk for remote exploits because of vulnerabilities in the platform’s URL protocol handler, researchers at ReVuln wrote in a paper released.
According to ThreatPost, Luigi Auriemma and Donato Ferrante discovered a number of memory corruption issues, including buffer and heap overflows that would allow an attacker to abuse the way the Steam client handles browser requests. Steam runs on Windows, Linux and Mac OSX.
The steam:// URL protocol is used to connect to game servers, load and uninstall games, backup files, run games and interact with news, profiles and download pages offered by Valve, the company that operates the platform. Attackers, Auriemma and Ferrante said, can abuse specific Steam commands via steam:// URLs to inject attacks and run other malicious code on victim machines.
Read more on the ThreatPost blog
Protect your gaming with BitDefender GameSafe
New Java vulnerabilities found just after release of recent update
Only hours after the latest Java update, yet another set of vulnerabilities were discovered by security researchers. Now, plagues the question: “Is the Java team doing a good job patching security holes and generally producing secure software code?” What the problem is, is that Java is being actively exploited in the wild. That means hackers and malware writers are naturally targeting Java because of its open holes.
Because Oracle went quite a while before fixing a vulnerability, hackers and malware writers are having a ball game with Java Runtime Environment. Most of these exploits are targeting the Windows OS. Researchers find only a matter of time before it affects the Mac OS platform.
According to CNET, “Oracle broke its quarterly update schedule for Java and released update 7 for the runtime; however, even after this update, yet more vulnerabilities have been found.”
If that’s not problematic enough, many antivirus companies are failing to block the latest exploits for the Java vulnerabilities. Some of the newer avenues of infection and exploits, including ZeroAccess/Sirefef, Java vulnerabilities continue repeatedly. It’s been going on, seems like for ages.
Many question how much Oracle cares about this situation, or not taking it seriously enough. All that can be done is to keep a watch, check for updates every few days, and actually apply the updates to be protected.
Kaspersky Anti-Virus 2013 brings you the essential antivirus technologies that your PC needs – in a product that’s easy to download, install and run. Kaspersky Anti-Virus 2013 works behind-the-scenes – defending you and your PC against viruses, spyware, Trojans, rootkits and other threats… all without significant impact on your PC’s performance. Click Here
Adobe Releases Subsequent Updates for 6 Flaws
New releases of update from Adobe come a week after their recent release, which was critical. Having subsequent updates for critical flaws begs the question of whether or not Flash Player is safe. Looks as if AIR was affected, as well. This patching closes six vulnerabilities, helping to safeguard against hackers.
These platforms are affected, and now have a patch available for download:
- Windows (New update: 11.4.402.265)
- Mac (New update: 11.4.402.265)
- Linux (New Update)
- Android (New Update)
The customized Google Chrome version (Pepper) should be automatically update to version 11.3.31.230 for PC and 11.4.402.265 for Mac.
For Windows and Mac users, bear in mind the new Adobe AIR 3.4.0.2540, which you should include with your updates for Flash Player.
Last week’s update included a critical flaw (CVE-2012-1535) in Adobe Flash Player.
For this week’s update, it fixes the following, according to Adobe:
- These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2012-4163, CVE-2012-4164, CVE-2012-4165, CVE-2012-4166).
- These updates resolve an integer overflow vulnerability that could lead to code execution (CVE-2012-4167).
- These updates resolve a cross-domain information leak vulnerability (CVE-2012-4168).
Rakshasa Case Study: Really Undetectable?
By Jay Pfoutz
Editor
Apparently, the new showy security threat is Rakshasa… At Black Hat Las Vegas, this new security technique was unveiled.
This new malware by researcher Jonathan Brossard is apparently ‘impossible to disinfect’.
Now, FIRST OF ALL!! – Anything created with man’s hands can be destroyed. I’d like to see this opinion last: undetectable, can’t be disinfected, etc.
The paper on Rakshasa can be found here. It describes a hardware backdoor. Unbeknownst to this artist researcher, companies like Kaspersky or ESET have already begun to craft hardware antivirus drivers. So, this backdoor hardware malware scheme is a bit late, but maybe just in time, too.
Will it be used? Who knows. That’s the scary part!
It is realistically a BIOSkit, a rootkit that infects the BIOS of the computer. What’s wrong with this…? It can be easily disinfected by flashing all of the devices of the computer, which apparently would be infected.
However, this malware has not been tested in an enterprise-based beta, which means just because it worked on a couple of machines does not mean it would work on any other computer. Impressive? Yes! But, not at all scary, yet.
What makes me more shocked, is that people will actually believe that this malware will not be able to be disinfected. But, this is the turnaround: it can be! This is nothing more than a BIOSkit, and we have seen BIOSkits removed in our leagues many times.
But, then again, people commonly believe rootkits are impossible to be removed too. Look…we proved them wrong!
By inflicting code signing for BIOS, just like all other hardware driver signing, can easily keep it blocked. Also, if BitLocker evolves in Windows 8 and further technologies, it could easily secure the OS. Also, things like device encryption, could be taken to a new level.
This is not a new vulnerability, and Brossard agrees.
I’m sure we’ll have more on this story as it develops in the future. Stay tuned to seCURE Connexion!